Again a new ransomware attack “aka Rapid Ransomware” has been surfaced. Similar to previous variants, Rapid Ransomware will scan the system for data files and encrypt them. This variant will append “.rapid” as extension to the encrypted file's name.
Once done with encrypting the system it will open "recovery.txt" ransom notes in Notepad. These ransom notes tell the victim to send an email to "frenkmoddy@tuta.io" to receive further instructions on restoring files and payment.
This post is an overview of the analysis been made by BluSapphire.
ANALYZED SAMPLE:
MD5: 46f5092fcedc2fee4bfbd572dd2a8f6f
BEHAVIORAL ANALYSIS:
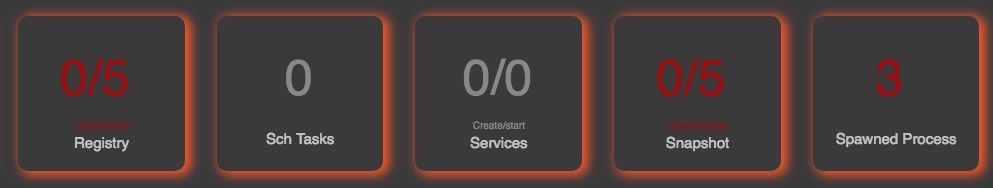
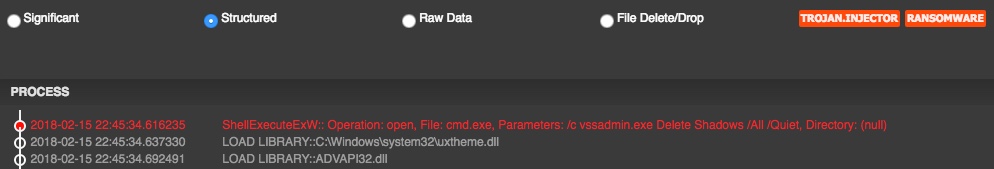
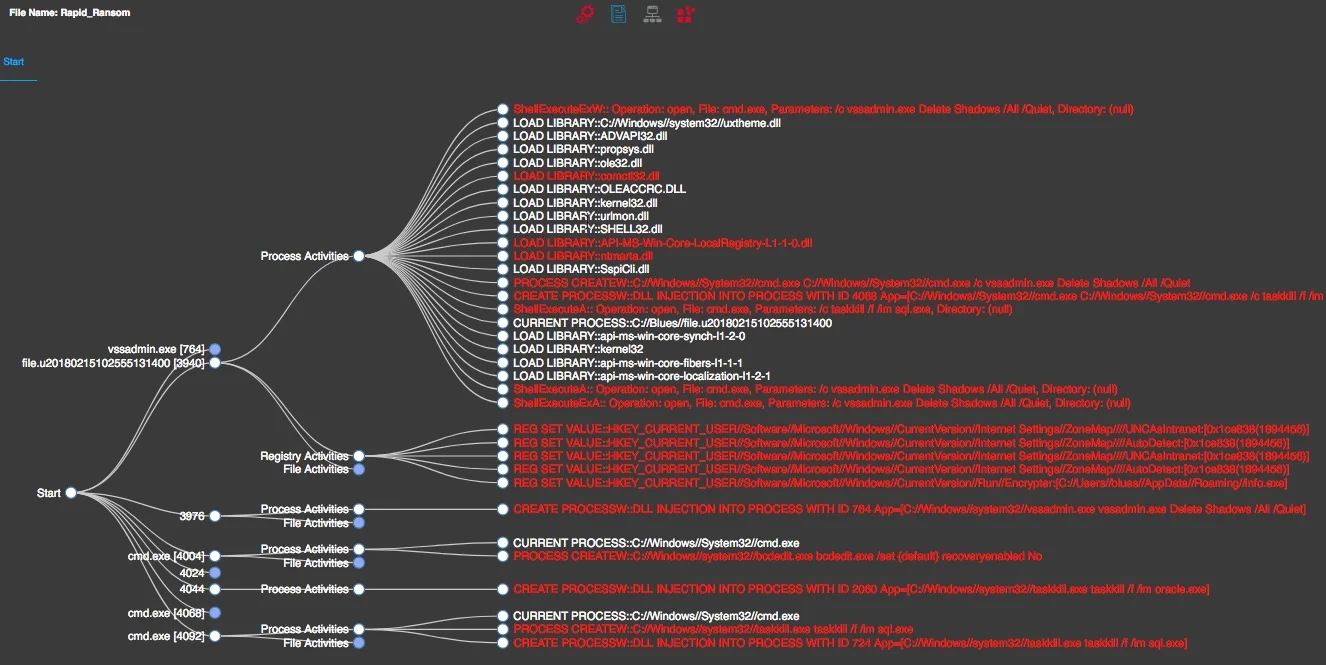
Upon execution of the sample, it deletes the existing shadow copies within the infected machine making it almost impossible to recover.
Attacker used windows utility "bcdedit.exe" and disabled windows automatic repair mode. Also executed "taskkill.exe" commands to kill any running database processes if they exists.
Noticed that the malware places a file named "info.exe" in folder "%APPDATA%/Roaming/" and configures itself to auto-run on every login by setting a new registry entry under key "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\".
With the ability to run on every logon, it appears that the malware is capable of checking for newly created files and encrypt them.
Unfortunately, As of this writing we haven't come across any methods that could help us decrypt the files encrypted by Rapid Ransomware.